Dynamic Auto Assessment - Simple but effective
edgescan provides our clients with #fullstack security assessments but what does #fullstack mean?
#fullstack covers may layers in the OSI inter-connectivity diagram.
From "the top down......"
Deep Coverage
Web Applications:
- Technical vulnerabilities (Injection attacks, scripting, error based attacks)
- Logical vulnerabilities
- Component Security (end-of-life components/plugins, insecure config)
Host Security:
- Patching
- Enabled services (Type, version, known vulnerabilities etc)
- Operating System Known vulnerabilities
- Weak protocols
- Weak configuration
So unlike many application-only or Host-only assessment services, edgescan discovers more possible weaknesses as a result of either via poor maintenance, configuration mistakes, deployment security, patching and also developer code....#fullstack
Wide Coverage
The holistic approach also covers ranges of IP's such as say a /24 or /16 cidr block.
Automatic Assessment:
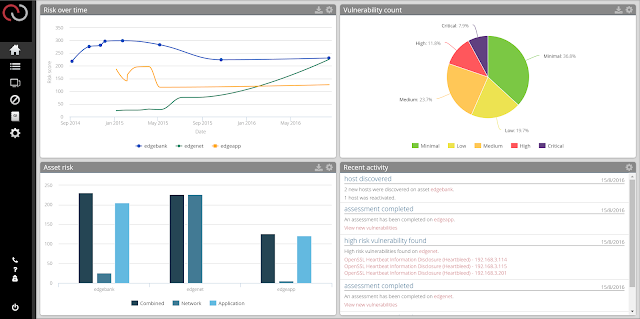
edgescan shall assess anything that is "live" at a given point in time across the entire block. We find this helps with the use case of rogue deployments, insecure services being deployed, APT, data ex-filtration servers etc
In the age of the cloud, organisations servers are constantly being spun-up and torn-down depending on demand. Our approach to range-based assessments covers this scenario as our clients know everything live within their range shall be detected and assessed.
Automatic vulnerability assessment coupled with continuous asset profiling provides our clients with a very adaptable solution when their systems are constantly in a state of flux.
No need for messy licensing or paper work for every assessment given our licensing is range based and we don't mind how many servers are live at any point in-time they shall all be assessed and the results manually validated in our SoC...
Alerting
edgescan also has alerting capability such as SMS, email and soon to be #slack alerting which shall be 2-way (think of it as a vulnerability management #slackbot).
You and ask edgescan to alert you if certain conditions arise such as:
- New asset discovered
- New Vulnerability Discovered
- Change in hosting environment
- Assessment cycle is completed
- etc etc
Risk Mitigation
Via our API you can now generate web layer mitigation rules for Web Application Firewalls (WAF) on demand (CItrix Netscalar and Mod_Security). This gives you the flexibility to virtually patch discovered issues very quickly using your underused WAF :)




Comments
Post a Comment