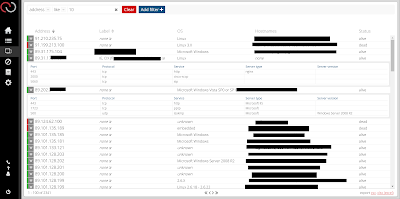
Dynamic Auto Assessment - Simple but effective
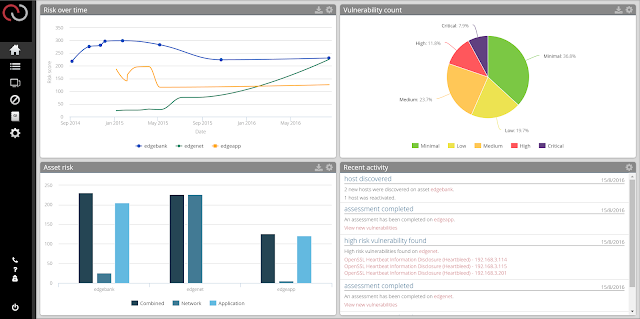
edgescan provides our clients with #fullstack security assessments but what does #fullstack mean? #fullstack covers may layers in the OSI inter-connectivity diagram . From "the top down......" Deep Coverage Web Applications : Technical vulnerabilities (Injection attacks, scripting, error based attacks) Logical vulnerabilities Component Security (end-of-life components/plugins, insecure config) Host Security : Patching Enabled services (Type, version, known vulnerabilities etc) Operating System Known vulnerabilities Weak protocols Weak configuration So unlike many application-only or Host-only assessment services, edgescan discovers more possible weaknesses as a result of either via poor maintenance, configuration mistakes, deployment security, patching and also developer code....#fullstack Wide Coverage The holistic approach also covers ranges of IP's such as say a /24 or /16 cidr block. Automatic Assessment : edgescan shall