Continuous Asset Profiling
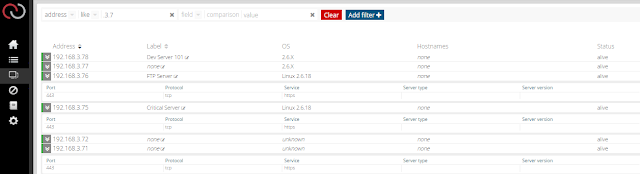
Continuous Asset Profiling Something we are pretty proud of at edgescan is our Continuous Asset Profiling service which is part of any edgescan license. We call it HIDE (Host Index, Discovery & Enumeration). So what is it and why should I care? HIDE provides continuous asset profiling across blocks of our clients IP's So rather than asking a client to specify individual IP's, edgescan profiles entire IP blocks/ranges. But why do this? The reason we give our clients the ability to profile entire blocks is three-fold. HIDE can detect if a server/IP goes live since the last round of continuous profiling. HIDE can detect if a new service / port or firewall change has occurred on any asset profiled. HIDE can alert our client of any change to their external asset profile on an ongoing basis using various methods such as SMS, email or Live Feed. If, as per traditional approaches to profiling, we only assess named endpoints we don't get the full picture. HIDE



